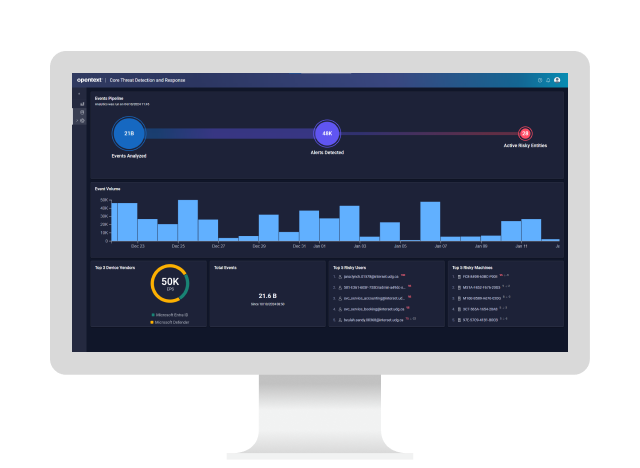
OpenText Core Threat Detection and Response
Identify hard-to-detect threats before they can cause damage
Insider threat detection
Stop wasting time on false positives—surface the threats that matter, faster. Empower your SOC with AI-driven detection that learns your environment and spots insider threats others miss.

OpenText™ Core Threat Detection and Response uses patented, self-learning behavioral analytics to detect insider threats, credential misuse, and subtle anomalies that evade rule-based tools. It continuously learns what is normal across users and systems and identifies deviations that signal risk—without manual tuning or added agents. Help your SOC reduce alert fatigue, prioritize response, and detect advanced threats with greater precision.
Why OpenText Core Threat Detection and Response?
Modernize security operations with adaptive AI that reduces alert fatigue, detects insider threats faster, and gives your team time back.
- Fewer
false positives with behavioral AI baselining
Detect threats based on deviations from each entity’s normal behavior not generic rules or signatures. - 10+
proven innovation patents with over a decade of patented research
Built on 10+ patented AI technologies for advanced behavioral detection and insider threat identification. - 80%
red team detection success rate with skilled threat hunters
Boost threat hunter accuracy with context-rich alerts that uncover stealthy attacks and accelerate investigations.
Use cases
Support SOC analysts, threat hunters, and security leaders with AI-powered detection that learns from your environment. Detect insider threats, reduce alert fatigue, and expose advanced attacks that traditional tools miss.
-
Identify malicious insiders, negligent behavior, and compromised accounts with self-learning behavioral analytics. Flag abnormal access, privilege misuse, and suspicious data movement—without relying on predefined rules.
-
Surface the threats that matter with adaptive AI that continuously prioritizes risk based on behavioral context. Let your SOC team stop chasing false alerts and stay focused on real threats.
-
Go beyond raw logs. Give threat hunters a head start with automatically surfaced behavioral threat indicators, risk-scored anomalies, and plain-language context that guides investigation.
-
Catch slow-moving, stealthy threats that blend in. Behavior-first detection spots the early signs of advanced attacks—even those without known signatures—before they escalate.
Key features
Modernize your SOC with self-learning behavioral analytics that prioritize real threats, reduce noise, and adapt as your environment evolves.

Behavioral analytics engine
Baselines user and entity behavior continuously to detect abnormal activity like credential misuse, lateral movement, and insider threats—without relying on rules or thresholds.

Unsupervised machine learning
Learns your organization’s “unique normal” with AI that automatically adjusts detection over time, improving precision as users, roles, and risk factors change.

Context-rich alerting
Delivers clear, prioritized alerts that explain what happened and why it matters—so analysts can respond faster without sifting through noise.

Risk-based prioritization
Examines behavioral severity, frequency, and peer comparison to dynamically score and rank threats—guiding attention to what’s truly urgent.

Microsoft ecosystem integration
Ingests telemetry from Microsoft Defender for Endpoint and Entra ID, enriching detection with behavioral analytics that enhance what Microsoft tools already see.

Visual investigation dashboards
Accelerates analyst decision making through fast triage and investigation with intuitive timelines, entity heat maps, and user behavior trends.
Accelerate the value of OpenText Core Threat Detection and Response
Integrations
Expand your security operations capabilities.
-
Minimize MTTD, MTTR with real-time threat detection and native SOAR
OpenText™ Enterprise Security Manager
-
Safeguard data, reduce risks, improve compliance, and govern access
Data security
-
Empower developers with trusted, reimagined application security
Application security testing
-
Defend against threats with real-time network monitoring and response
OpenText™ Network Detection and Response
-
Secure your digital assets by confidently managing identities and access
Identity and access management
Professional Services
OpenText Professional Services combines end-to-end solution implementation with comprehensive technology services to help improve systems.
-
Accelerate your journey to enhanced threat detection
OpenText™ Core Threat Detection and Response Managed Security Services
Partners
OpenText helps customers find the right solution, the right support, and the right outcome.
-
Search OpenText's Partner directory
Find a Partner
-
Explore OpenText's Partner solutions catalog
Application Marketplace
-
Industry-leading organizations that enhance OpenText products and solutions
Strategic Partners
Communities
Explore our OpenText communities. Connect with individuals and companies to get insight and support. Get involved in the discussion.
-
Explore and vote on ideas, participate in the forums, and network with your peers
OpenText Enterprise Cybersecurity Community
-
Expert insights, threat intel, and product updates—built for SMBs
OpenText Cybersecurity SMB Community
Premium Support
Optimize the value of your OpenText solution with dedicated experts who provide mission-critical support for your complex IT environment.
OpenText Core Threat Detection and Response resources
OpenText Core Threat Detection and Response
Read the product overviewThreat detection and response solutions comparison checklist
Learn more5 ways to elevate cyber defense against insider threats
Learn moreBehavioral analytics: Boost your SOC team’s threat detection and response
View the infographicOpenText Core Threat Detection and Response
Read the product overviewThreat detection and response solutions comparison checklist
Learn more5 ways to elevate cyber defense against insider threats
Learn moreBehavioral analytics: Boost your SOC team’s threat detection and response
View the infographic-
The solution uses unsupervised behavioral analytics to baseline every user and device across Defender for Endpoint and Entra ID telemetry, then flags even slight drift. Peer-group context surfaces malicious, negligent, or compromised insiders early—before privilege abuse or data theft can unfold.
-
Patented ML pipelines build multi-dimensional behavioral baselines for every entity and update continuously. This adaptive AI uncovers zero-day TTPs and low-noise anomalies missed by signatures, rules, or SIEMs, delivering higher-fidelity detections with almost no tuning.
-
SaaS onboarding through native Microsoft APIs is agentless and fast. Point to your tenants, backfill 30 days of history, and actionable detections appear within hours. Full behavioral maturity lands after about two weeks, giving SOCs insight long before traditional rule tuning finishes.
-
Integrated risk scoring suppresses benign anomalies, clusters related indicators, and elevates only high-impact events. The result: up to 90 percent fewer false positives, drastically reduced alert fatigue, and analysts who can focus energy on genuine threats instead of drowning in noise.
-
Online learning refreshes baselines daily, automatically absorbing role changes, shift rotations, mergers, seasonal peaks, and travel patterns. Detection precision remains tight without rule rewrites, keeping insider-threat coverage accurate as the business and its workforce evolve over time.
-
Every alert is tagged with ATT&CK tactic, technique, and step; an LLM-generated narrative links precursor activity to follow-on actions. Analysts know their exact kill-chain position, prior context, and recommended next moves, shortening triage and speeding containment.
A new era of advanced threat detection and response has arrived
Read the blogCan you spot the threat? OpenText Core Threat Detection and Response can
Watch the videoA new era of advanced threat detection and response has arrived
Read the blogCan you spot the threat? OpenText Core Threat Detection and Response can
Watch the video
Take the next step